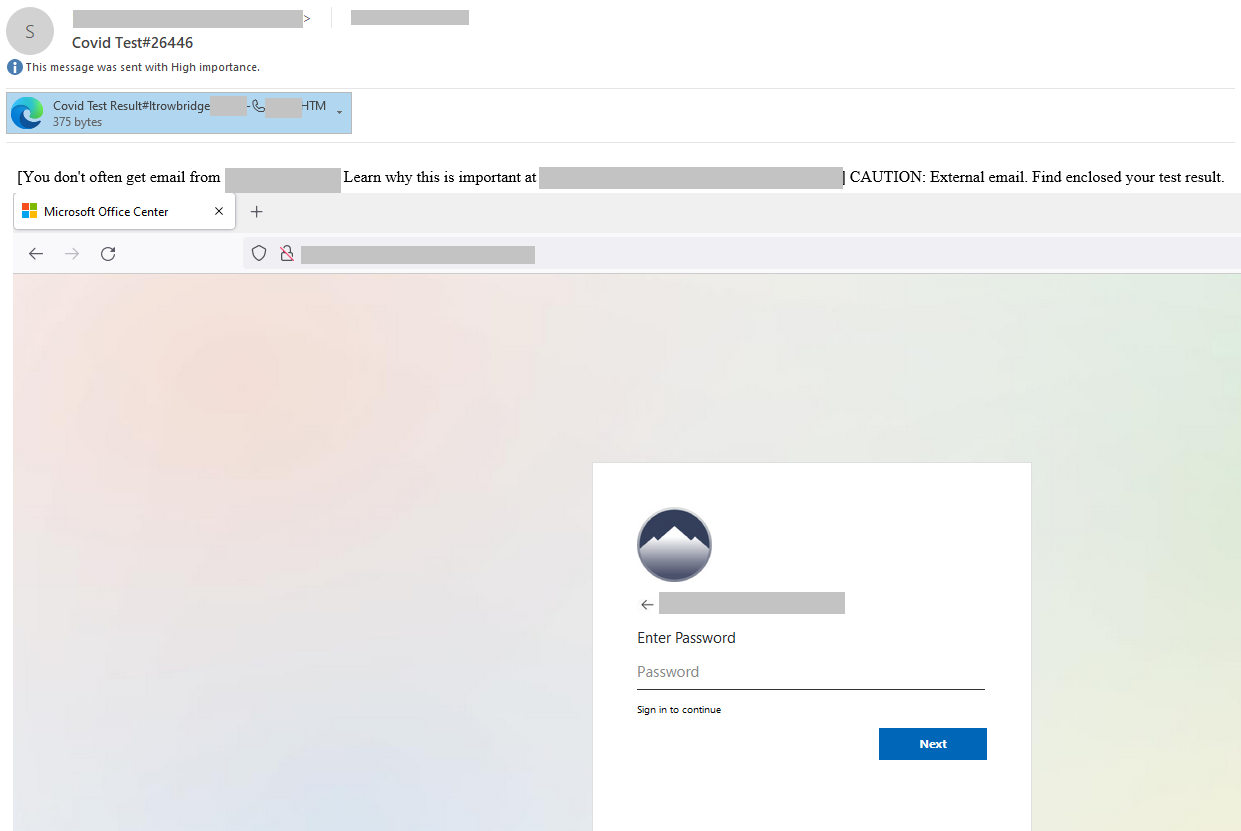
Phishing is the means of duplication or replicating the first articles that resides online and provide an impression to your audience that it must be genuine as well as the end user will click on it. Due to that, the person will reveal the information and it might be something similar to charge card specifics or some kind of password of the website. A beacon or possibly a dessert can save that info in a form of a log. These logs are then given to the attacker and they can be then employed for a lot of functions and also the consumer will probably be unknown of most these pursuits.
Phishing can reproduce complete websites or some pages dependant upon the will need and by using different tools, it has become less complicated to the attacker to do their pursuits and spy on any enterprise with their option and they can keep completely anonymous. With the help of these excellent resources, your job of phishing will certainly be a great deal much easier to conduct and they tools are available for you as application and programs.
Fetching Personal Information
This exercise is most frequent nowadays when hackers deliver analtered e-mail that looks to be coming from a legitimate resource but the truth is quite the exact opposite as it is an easy method of stealing sensitive details. The main stuff that are fetched in cases like this will be the credit card details and login specifics.
Manipulation with Content
Information has the ability to accomplish nearly anything and the identical is the case if we focus on hacking as possible power an individual to simply click a selected website link just by producing your posts far more attractive and by alluring on the user. Additionally it is a method of stealing details these days and it can either be performed by a fabricated fudpage or by developing bogus web sites.